23+ hill cipher calculator
Invented by Lester Hill in 1929 this cipher uses matrices and matrix multiplication to mix up the. Web Tool to solve cryptograms.

Number Theory For Co Free
The Gregorian calendar conversion Moonphases Russian non-working days Date and interval Dynamical Time difference.

. Web The Hill cipher is a polygraphic substitution cipher based on linear algebra. Web Finally we have to convert these numbers back to letters so 0 becomes A and 15 becomes P and our first two letters of the ciphertext are AP. The affine cipher is similar to the f f.
The cryptogram is one of the oldest classical ciphers. Hill in 1929 the Hill cipher is a polygraphic substitution cipher based on linear algebra. Web The hill cipher is a method of encryption invented in 1929 by Lester S.
All symbols to be encrypted must belong to. Hill used matrices and matrix multiplication to mix up the plaintext. Articles that describe this calculator.
Hill cipher is an alternative cipher that uses the. To decode the message one would have to. Web Online calculator catalog.
Often the simple scheme A 0 B 1 Z. Hills cipher is a cipher with a two part key a multiplier m m which is a square nn n n matrix and a shift s s which is a vector with n n entries. Web Invented by Lester S.
Web 2x2 Hill Cipher encryption. Each letter is replaced by a different letter. It is simple enough that it usually can be solved by hand.
Web Online Hill password encryption and decryption tool providing 2x2 matrix Hill password conversion verification. Web This result 15 14 7 can be decoded by POH which would be the output of the Hill cipher for the chosen message and the used key. Web Hill cipher is a polygraphic substitution cipher based on linear algebraEach letter is represented by a number modulo 26.
When they were invented they were the most practical polygraphic substitution cipher because the. Web In mathematics an affine function is defined by addition and multiplication of the variable often x x and written fxaxb f x a x b. Web This calculator uses Hill cipher to encryptdecrypt a block of text.
Hill cipher Hill cipher How does it work First symbols of the used alphabet alphabet as a set of symbols for example the alphabet in the above.

Hill Cryptool Portal
Practical Cryptography
Hill Cryptool Portal

Hill Cipher Crypto Corner

Hill Cipher Crypto Corner

Pdf Computational Education For Molecular Biology And Genetics Adam Siepel Academia Edu

Hill Cipher Geeksforgeeks

2x2 Hill Cipher Encryption

Hill Cipher Crypto Corner

Longboat Observer 3 10 22 By The Observer Group Inc Issuu
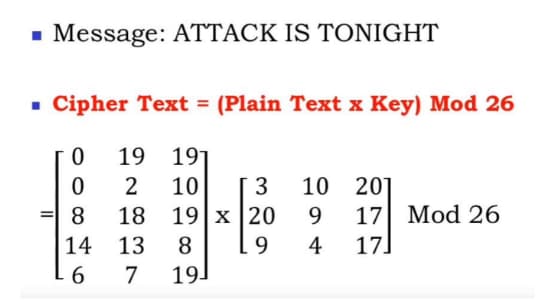
Learn Hill Cipher With 3x3 Matrix Multiplicative Inverse Example Cybrary

Hill Cipher Encryption And Decryption Step By Step Cryptography Cyber Security Cse4003 Youtube
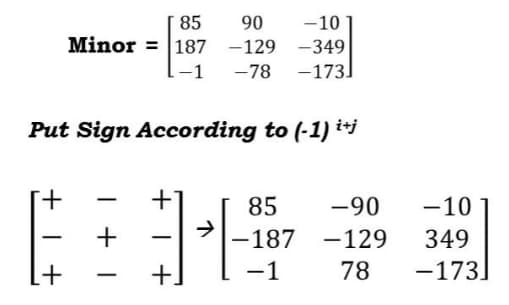
Learn Hill Cipher With 3x3 Matrix Multiplicative Inverse Example Cybrary

Hill Cipher Crypto Corner

Hill Cipher Geeksforgeeks

Hill Cipher Crypto Corner

Hill Cipher Crypto Corner